So Microsoft has released the new wave of products into preview, including the next version of Katal (Azure Services) for Microsoft, called Azure Pack. This pack transforms your datacenter into Azure allowing users to sign up using plans and be able to use your infrastructure into a IaaS platform.
You can download the trial for Azure Pack here –> http://www.microsoft.com/en-us/server-cloud/windows-azure-pack.aspx
Now there are some prerequisites for using this pack.
You can read more about them here –> http://technet.microsoft.com/en-us/library/dn296442.aspx
But in order to integrate Azure pack with your on-premise solution it uses Service Provider Foundation (Which is included in the Orchestrator installation media)

Not that this requires the installation of SCVMM 2012 R2 Console on the same machine as SPF since it uses the VMM APIs to communicate with it.
It also requires some other prerequisites such as

WCF Data Services 5.0 can be found here –> http://www.microsoft.com/en-us/download/details.aspx?id=29306
.NET features 4.5 WCF is a part of .Net 4.5 which can be installed from Server Manager
Management ODATA IIS is also a part of 2012 R2 installation media
ASP.NET MVC 4 can be downloaded from here –> http://www.asp.net/mvc/mvc4
Next we configure a database for use for SPF

In this database the SPF stores information such as
Tenants
Usage Records
Gallery Items
Roles
Servers
And Tenants Stamps
Next we choose where to deploy the SPF files and what certificate we want to use.
In my case for this demo I used a self-signed certificate.

Next we define credentials for the admin web service

NOTE: If you choose Network Service here you need to make sure that the machine account is a VMM administrator
In my case I choose a Service Account and entered a domain user.
After that you are done with SPF

Next we move on to the Azure Pack installation
You can download the pack from here –> http://technet.microsoft.com/en-us/library/dn296435.aspx?CR_CC=200142594
All it does is download a profile which uses webdeploy.

Now by default it will install all the web roles on the same servere

Click I accept (ill come back to what the different roles do)
And Note this installing part may take some time.
After that is done, press Continue and ill will start the Service Management Configuration site.

It will open a browser window on the localhost on port 30101, and again we will have to define a Database and server for the Azure Pack.
Here you have the option to use a Windows user or a regular SQL user.
Remember that you have to enable Mixed Mode on the SQL server in order to use regular SQL users.

Make sure that you write down the passphrase. If you forget or lose this passphrase, there is no way to recover it. This is used to encrypt and decrypt the Configuration Store..
Next we define a FQDN for the host

After this is done it will start configuring the different roles on the Server

After that is done we continue on with the configuration

NOTE: You may need to log out of your system and log back in before you can access the management portal for administrators. This is due to Windows authentication and the need to add the security group to your security token.
If you continue to see an access denied error, even after logging back in, close all Internet Explorer windows, and run Internet Explorer as an administrator.
Now the setup will open a browser on port 30091 which is the default port for the management portal for administrators
Now you can see the difference between “Katal” and Azure Pack
Katal (The old version)

(Azure Pack the New one)

New stuff is including
Reporting provider (This is also a feature that is on the Orchestrator installation media)
Service Bus Clouds (Read more about setting up service bus here –> http://msdn.microsoft.com/en-us/library/windowsazure/dn282152(v=azure.10).aspx )
Automation (This requires Service Management Automation web service)
So in my case I define the Service Provider Foundation endpoint for Azure Pack
And then Go to VM Clouds and connect to my VMM Management Server.
Add some bugs when connecting to my cloud but after a IISreset it worked just fine

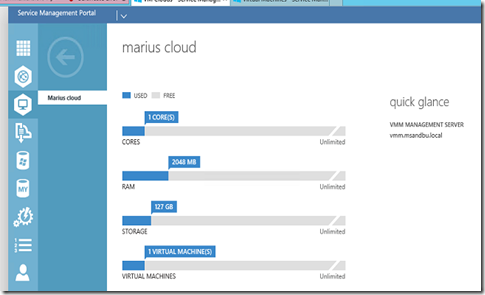
This gets the cloud container from VMM, from here I can view resources in my cloud
Now for the end-user I can sign up using the tenant portal.
Which is on the same server you installed Azure Pack only on port 30081 remember thou that you need to create a plan and publish it in order for users to subscribe to that plan.
Here I signed up with a regular user account

Choose Add Plan and select a public plan which was created on the management portal.
Note thou that here we have external users created we can also use AD authentication
For the tenant portal you can configure this using ADFS here –> http://technet.microsoft.com/en-us/library/dn296436.aspx#WAP_AddADFSAuth
Note when you sign up for a plan you need to go back to the administration portal and approve the subscription.
Now If I want to automate a task associated with VM create I can do this in the management portal

All for this time, all dive in a bit more when I got the time 
Stay tuned
#active-directory, #azure, #service-provider-foundation, #system-center-2012, #windows-server-2012, #windows-server-2012-r2



![]()